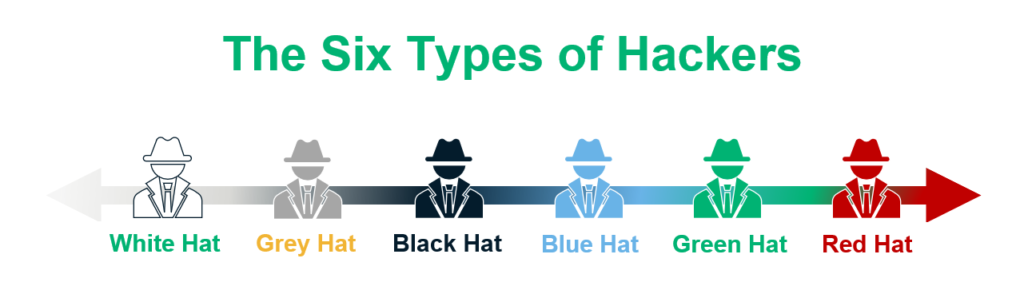
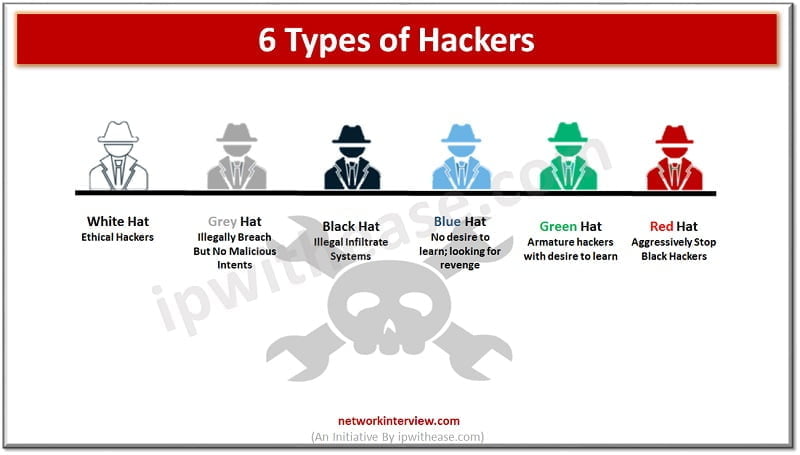
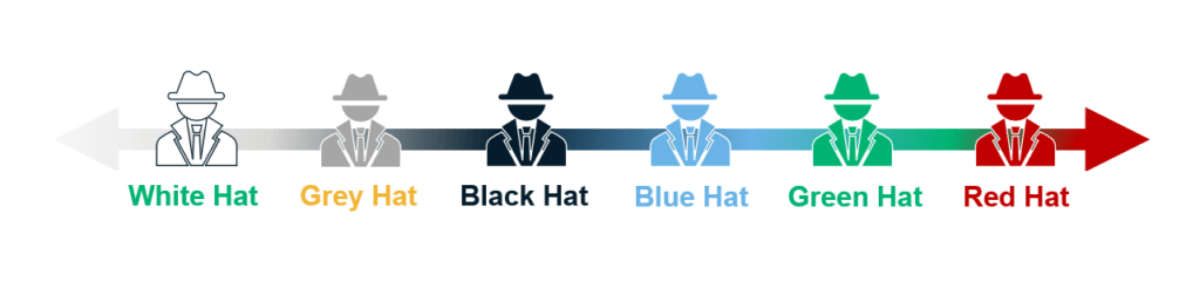
White Hat, Red Hat and all the colours in between. What are the different types of Hackers? | InConsult

7 types of computer hackers - White hat, Gray hat, Black hat, Green hat, Blue hat, Red hat - YouTube

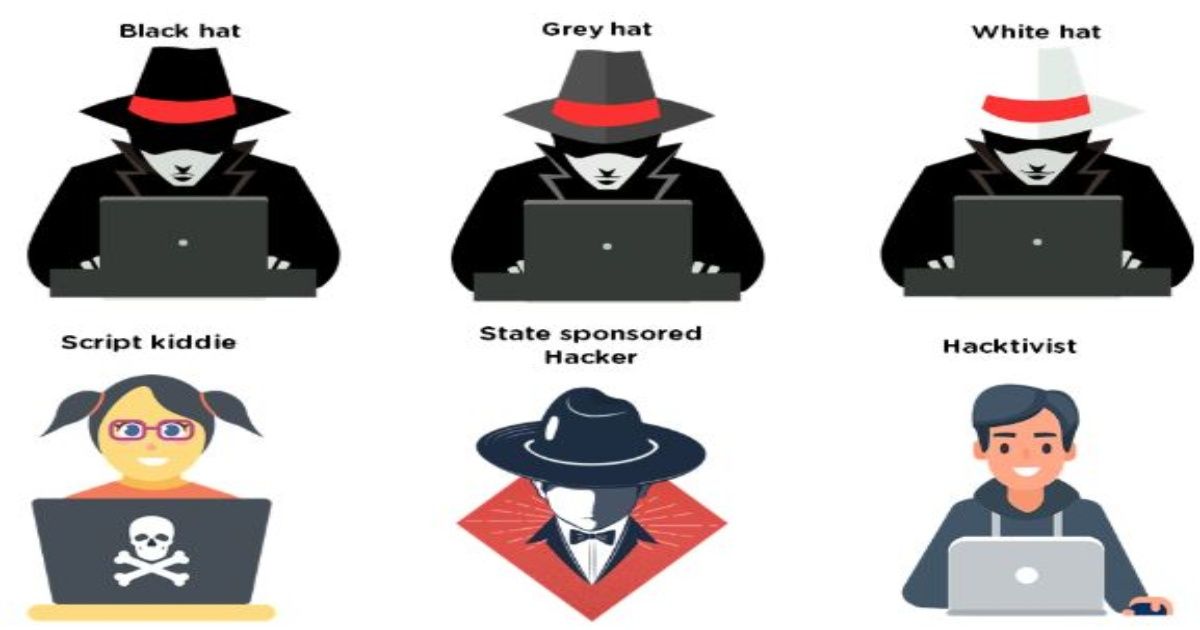
Giuliano Liguori on Twitter: "#Infographic: Types of #Hackers Via @ingliguori White Hat Hackers Black Hat Hackers Gray Hat Hackers Script Kiddies Green Hat Hackers Blue Hat Hackers Red Hat Hackers State/Nation Sponsored